Infrastructure templating in сloud-native environments
- Created at:
- Updated at:
In today's cloud-native landscape, infrastructure templating plays a pivotal role in simplifying the intricate processes associated with infrastructure development and maintenance. This approach offers multifaceted benefits:
- Facilitating Easier Infrastructure Development. By delineating functional borders, infrastructure templating streamlines infrastructure development processes. It provides a structured framework that aids in conceptualizing and defining infrastructure components, fostering clarity and precision in their development.
- Testing Interoperability Across Diverse Technologies. Infrastructure templating enables seamless testing of component interoperability, even when employing disparate technologies. This ensures smooth interactions and compatibility within complex infrastructures, regardless of the technologies used.
- Enabling Shared Infrastructure Patterns. The capability to share standardized infrastructure patterns across teams is another fundamental advantage. Templating allows for easy collaboration among team members, providing them with standardized templates that enhance understanding and utilization across an organization.
- Shipping Infrastructure with Products. The integration of infrastructure as part of the product significantly simplifies adoption processes for enterprise solutions. Vendors can bundle complex business applications along with infrastructure templates, streamlining setup complexities for end-users.
- Division of Team Responsibilities. Templating allows for a clear division of responsibilities between Platform and SRE teams. While the Platform team creates infrastructure patterns, the SRE team deploys and operates these patterns in production environments. Additionally, developers and QA engineers can utilize the same Infra Template to spawn temporary dev and test infrastructures.
- Leveraging GitOps Approach. The adoption of infrastructure templating enables businesses to fully leverage the GitOps approach across all infrastructure components. This approach ensures versioning, traceability, and automation, aligning infrastructure management with version control system principles.
Use Cases of Infrastructure Templating
Infrastructure Development and Promotion
An essential use case involves establishing pipelines for developing and promoting features across various environments, similar to deploying and testing applications. Leveraging common infrastructure templates and version control through Git integration streamlines integration with existing CI/CD solutions to ensure consistency and reliability.
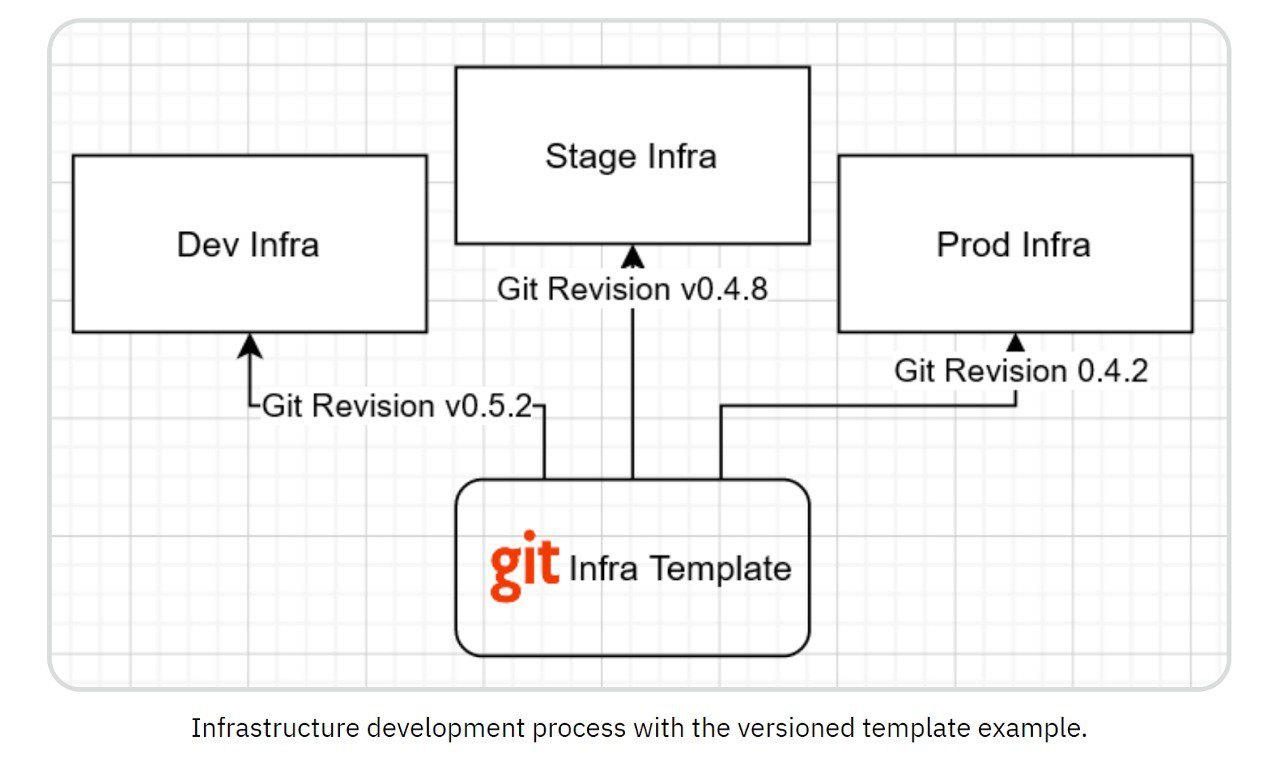
Segregation of Team Responsibilities
As organizations grow and multiple teams are established, clear segregation of responsibilities becomes crucial. The Platform team, responsible for creating infrastructure patterns, can provide these patterns as complete Infra Templates to the SRE team for deploying and operating production infrastructures. This enables developers and QA engineers to effortlessly create temporary dev and test infrastructures.
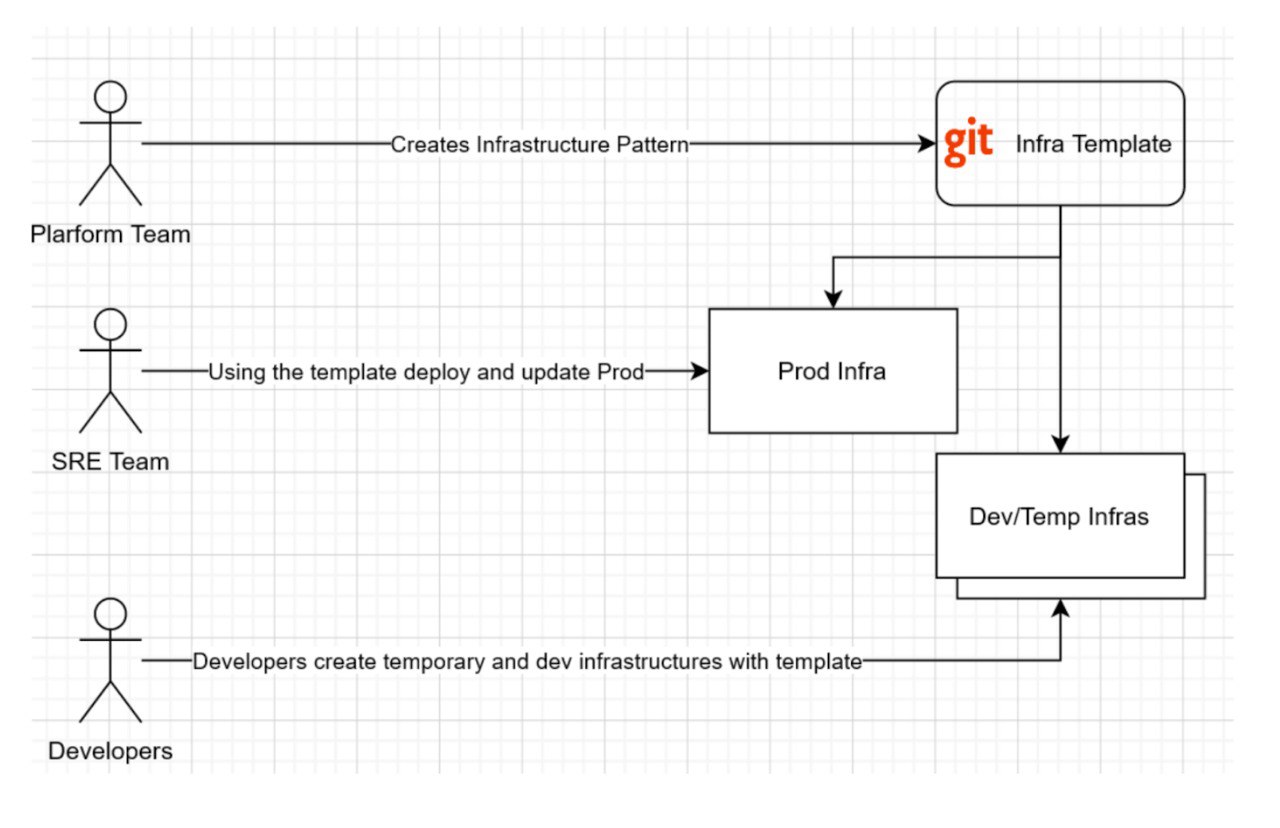
Software Shipment with Infrastructure Templates
Complex business applications often necessitate pre-deployed infrastructures. Vendors can simplify the adoption process by shipping their products alongside infrastructure templates, facilitating seamless setup for enterprise solutions.
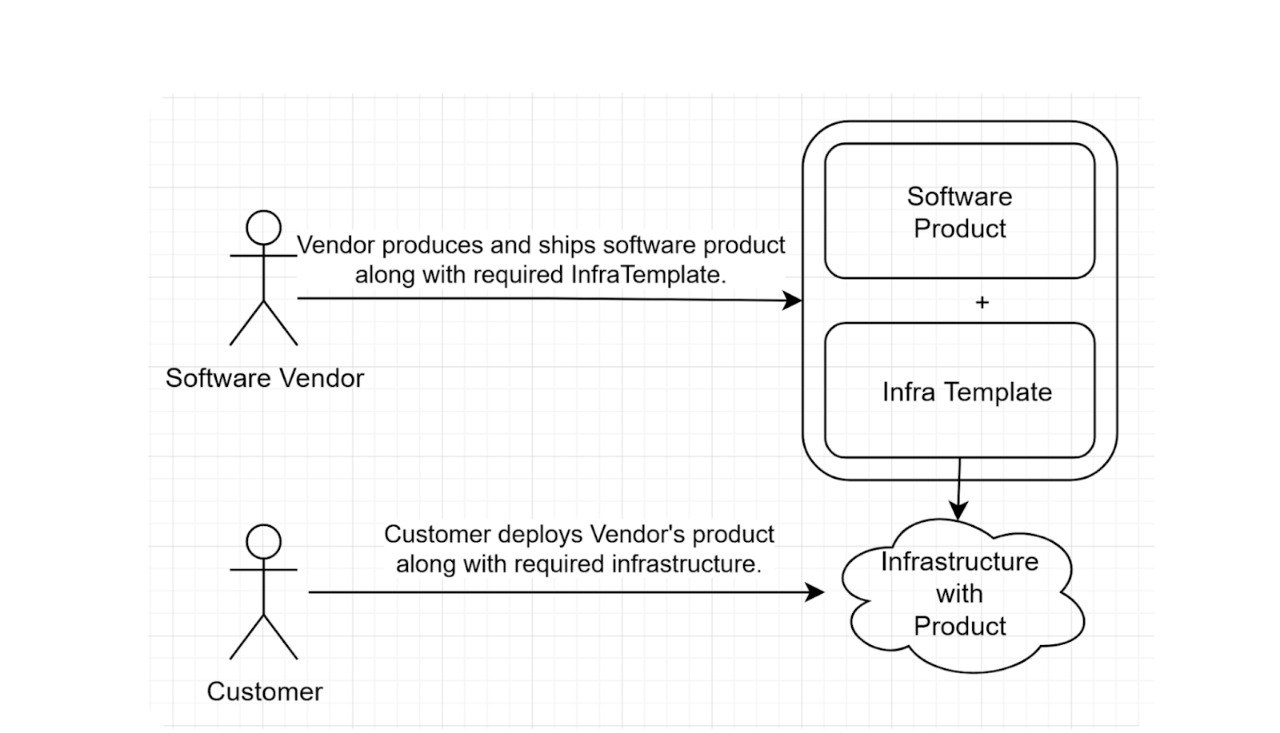
Utilization of Template Market
In scenarios where engineers require new infrastructure for testing or exploration, accessing templates from repositories or marketplaces enables swift infrastructure setup by configuring values and spawning the required infrastructure within minutes.
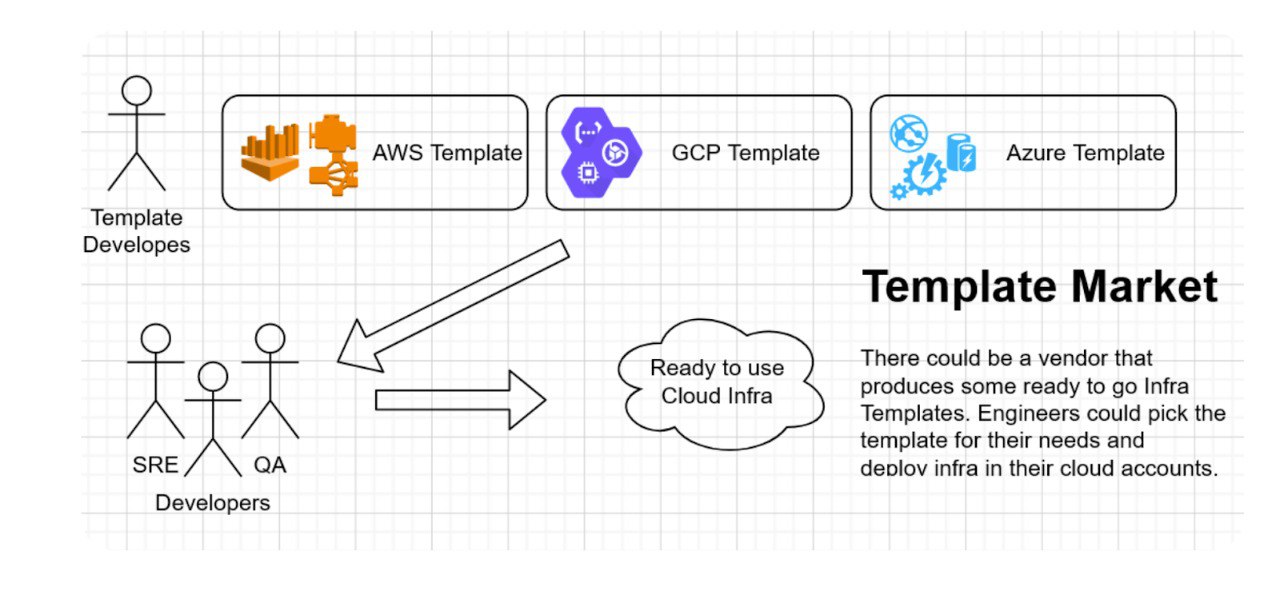
The Components of Infrastructure Templates
Infrastructure Layering
Cloud-native infrastructures are comprised of multiple layers:
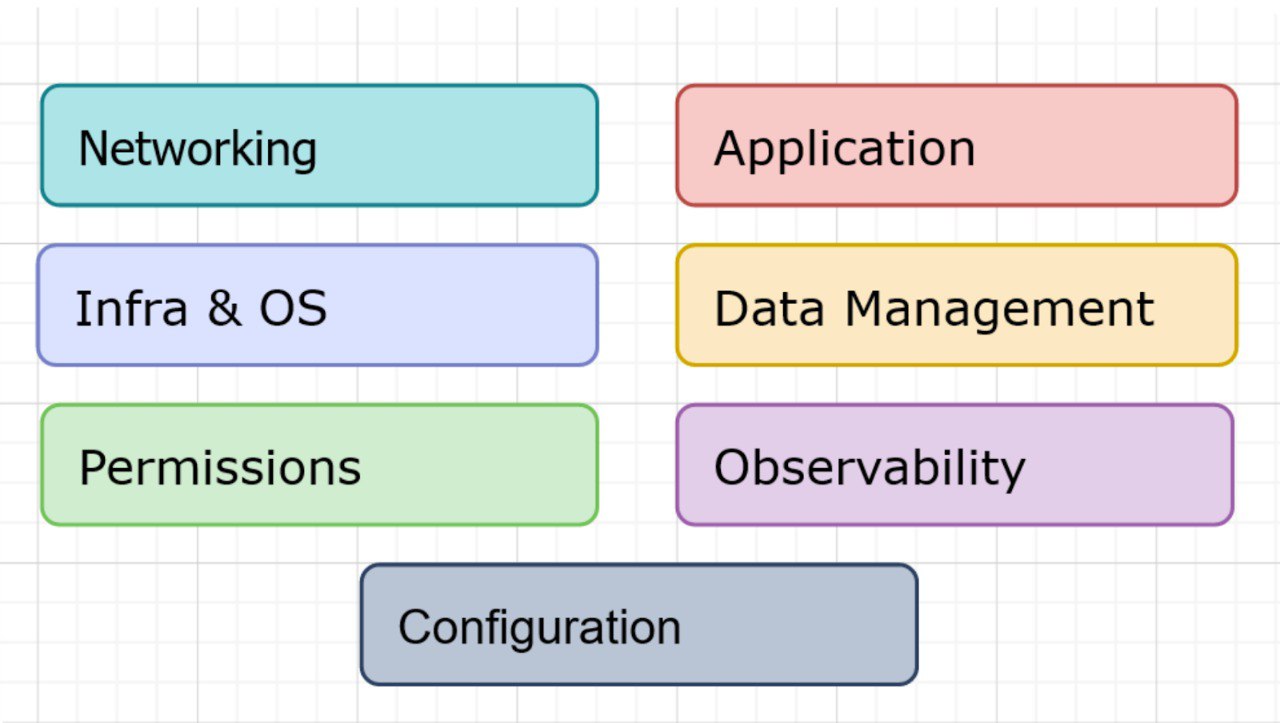
- Networking Layer: VPCs, Peerings, VPNs, Security Groups, and Routing.
- Permissions Layer: IAM roles and user policies.
- Infra and OS Layer: Server instances provision and operating system settings.
- Data Management Layer: Relational and NoSQL databases, caches, file, and object storages.
- Application Layer: Container orchestration, continuous delivery, and different application types.
- Observability Layer: Monitoring, metric logs, and tracing applications.
- Configuration Layer: Declarative configuration storage and secret storages.
Implementing Technologies for Each Layer
Networking Layer
Modern clouds offer Software Defined Networks and APIs for network declaration. Terraform modules facilitate the creation of cloud networks and Kubernetes networking.
There are two common approaches to this. The first is to use Terraform modules designed to define the cloud network for your project, for example: Terraform module which creates VPC resources on AWS,
Terraform code and scripts for deploying a GCP Virtual Private Cloud (VPC) and Terraform Azure RM Module for Network. Alternatively, when you need to define networking inside your container orchestration layer (ex Kubernetes) there are plenty of options using network plugins (CNI). In most cases the tools are delivered as Helm charts along with Kubernetes manifests.
Permissions Layer
Fine-grained permissions are managed using Terraform modules for IAM, Roles, and native RBAC in Kubernetes. Technologies including AWS IRSA, Azure Managed Identities, and GKE Workload Identity link permissions within Kubernetes to cloud roles. In such instances, you need to combine Terraform modules with Kubernetes manifests, getting outputs from one technology and passing them to another.
The infrastructure permissions could be set with Terraform modules for IAM and Roles, for example: Terraform module which creates IAM resources on AWS, Terraform module to manage multiple IAM roles for resources on Google Cloud. Both permissions and policy enforcement are mostly done using Open Policy Agent.
Infra and OS Layer
The Terraform modules Terraform module Auto Scaling resources on AWS, Terraform module for configuring GKE clusters and Azure compute Terraform module enable the declaration of infrastructure layers, supplemented by configurations added to images using cloud-init, Packer, or Ansible for comprehensive setup.
Data Management Layer
Most cloud providers offer managed storages and databases, such as AWS S3/EBS, GCP Cloud Storage, and Azure file/blob storage. Terraform modules facilitate the efficient declaration and management of these resources.
Application Layer
Cloud-native applications, classified into Infrastructure and Business Applications, are deployed using tools like Helm charts, bash scripts, or CI/CD platforms such as Jenkins and GitLab.
Observability Layer
Cloud-provided or external monitoring solutions, supported by Terraform, facilitate monitoring and logging in cloud-native environments. EFK or Prometheus/Grafana is often deployed with Terraform or Helm charts for cluster observability.
Configuration Layer
Storing configuration and infrastructure declarations in Git repositories allows for versioning and accountability. It's crucial to maintain infrastructure state in separate storage to safeguard sensitive data. Cloud-specific storages or external tools like Hashicorp Vault or SOPS ensure secure storage of secrets and certificates.
Conclusion
Infrastructure templating stands not only as a convenience but as a necessity in today's cloud-native landscape. Cluster.dev, an infrastructure templating engine, is designed to help you optimize infrastructure management within your organization.
This powerful cloud automation tool streamlines the processes of infrastructure development, testing, deployment, and maintenance, ensuring maximum operational efficiency of your systems.
No additional information provided by user.
Popular posts
-
6 Clever Hacks to Skyrocket Your Mobile Organic Search Traffic
- 1
- 0
-
Is Your Website Ready for These 28 Types of DDoS Attacks?
- 1
- 0
-
Challenges of adapting blockchain to the Internet of Things
- 0
- 0
-
Using Open edX: Definitive guide
- 0
- 0
-
Key iOS 15 updates for everyday users
- 0
- 0
-
Kids and gadgets: friends or foes?
- 1
- 0
