
Get money for software reviews
Leave thoughtful review and gain regular revenue. Learn more about reviews
This software for several years saves my PC. It has removed a lot of browser's toolbars and malware that can be installed together with some games or programs. That is good that it is free and I can download it at any time. I'm used to maximum performance of my computer and therefore try to remove unnecessary software that can affect the performance of my PC. I periodically download the latest version and install it. Then I run the scan and remove found issues. After these operations I uninstall MalwareBytes. It does not have much impact on the performance of my computer, but in any case, I never leave it installed. Definitely recommend and even shopping!

Malwarebytes is a cybersecurity anti-malware program. Anti-malware is a vital software today providing protection against malicious files and infected sites. It detects and removes adware, worms, trojans, rootkits, dialers, spyware, and ransomware. Malwarebytes has a unique set of features that many antivirus packages lack, and as it provides a bit different kind of protection, it is not recommended as a replacement for antivirus. The best option is to combine Malwarebytes and antivirus and thus, apply layered security.
Malwarebytes is available for Microsoft Windows, macOS, Android, and iOS. Current product version is 3.6.1.2711. There are Personal and Business packages. You can install Free edition for personal use on Windows. Premium edition provides not only remediation but also protection, for instance, against dangerous links. There are four Business packages:
Malwarebytes hardware requirements for Windows:
You can choose a version appropriate for business: standalone or managed. The standalone solution is perfect for teams and small offices; it implies no central management. Malwarebytes Endpoint Security is a perfect choice for business and enterprise. It combines protection and remediation technologies for multi-layer defense. Each version has separate technical specifications, which can be configured by the Management Console.
Management Console hardware requirements:
Mac Remediation hardware requirements:
Here is Malwarebytes in action:
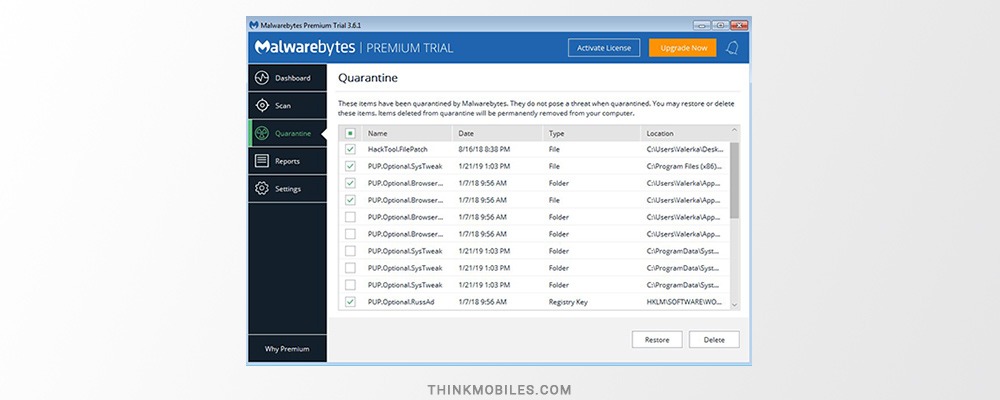
This popular anti-malware product surely has an intuitive interface. Dashboard section displays all information of current importance: the date of last and next (scheduled) scan, real-time protection settings, available malware database updates. Scan section serves to review the results of last scan and scheduling check-ups. We’ll describe scan options below. In this tab, you can also export scanning summary. Quarantine section shows all the files and folders placed by Malwarebytes in an isolated folder where they can cause no harm.
Reports section stores data about recent activities. Settings section contains several tabs. In the Application tab, you can select update options, display language, manage notifications, enable Proxy Server, collect event log data, etc. You can also schedule a scan in the appropriate tab of the Settings section. You can choose scan priority - at high priority scanning will take minimum time but may affect other tasks. With lower scan priority it will take longer to scan everything.
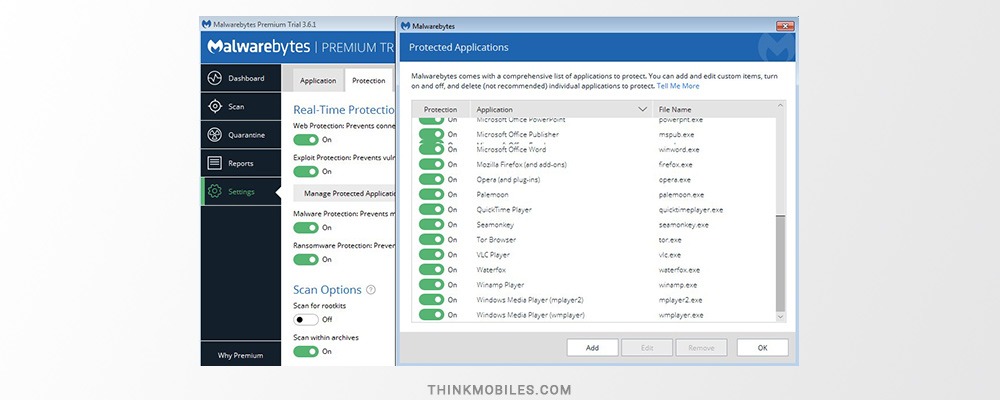
Protection tab contains all necessary settings for real-time protection, scans, and potential threat protection (including unwanted programs and modifications), quarantine and startup options. Also, you can add or remove applications for shielding in a Manage Protected Applications option.
In the Exclusions tab of Settings, you can exclude items from detection: files, folders, websites, apps or exploits (previously detected attacks). Later on, you can manage or remove exclusions in the same tab. In Settings users can view information about the product and your account details too. Notifications about blocked attacks sometimes appear on the screen and scanning speed is pleasant - it really does not slow down a device.
For first 14 days Malwarebytes free version offers real-time protection and a full set of Premium services. After that period, if a user does not buy a license, it downgrades to a limited version that can only clear your computer after an attack.
Paid plans pricing depend on the number of devices and subscription terms. Personal edition costs $39.99 for 12 months/1 device, $69.98 for 24 months/ 1 device. For 2 devices: 1 year subscription costs $49.99 and 2 year subscription is $87.48. For 10 devices: 1 year subscription is $129.99, 2 year subscription costs $227.48.
Business pricing for 2 devices:
Business pricing for 5 devices:
Business pricing for 10 devices:
For Enterprise edition one has to contact a sales manager and request a quote.
Malwarebytes offers three types of scanning: Threat Scan, Custom Scan, Hyper Scan. Threat Scan is launched daily by default. It takes the longest but checks a computer most thoroughly. This scanning method detects a majority of threats. It doesn’t scan literally every file on a PC but checks the locations where typically malware attacks happen:
With Custom Scan a user can choose what and where you want Malwarebytes for Windows to scan. To customize a scan, click the Custom Scan option, then click Configure Scan. With this option, you can choose areas to scan. In addition to memory objects, startup and registry objects, users can scan the following items:
Custom scan also allows to choose a particular folder or a file, as well as exclude items from scanning.
Hyper Scan mode is for instant detection of active threats and their removal. It in Malwarebytes app searches for threats in memory and startup objects. It is fast but not that thorough. Only Premium users have access to this service. If Hyper Scan catches any immediate threats, it is a good idea to run additional Threat Scan.
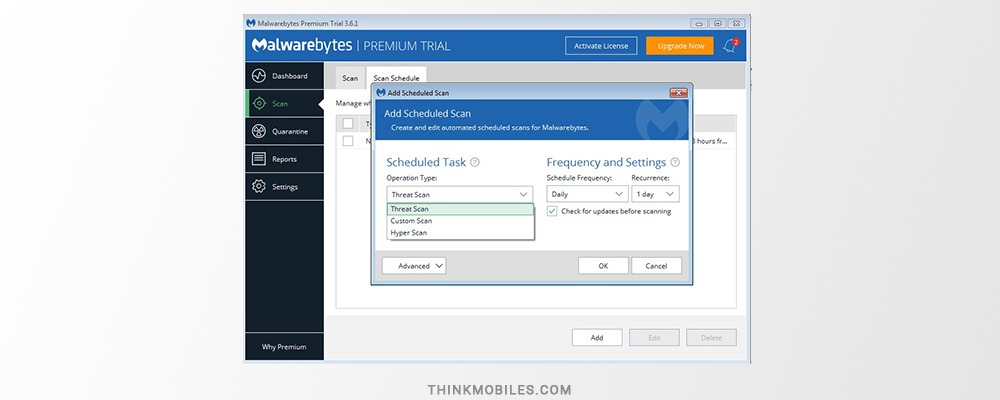
If you are a Premium edition user, you can schedule a scan, edit its details or remove it. To add the schedule, go to Scan schedule tab and press Add. Then, choose the scan type, date and time, frequency and recurrence. You can choose to quarantine all threats automatically or to receive a notification each time a new threat is detected, and decide on the action Malwarebytes should take.
We should mention that sometimes a legitimate file can be categorized as malicious and in this case automated quarantine might have unexpected implications. Select whether a computer will immediately restart after removing a threat or manually. Also, there's an option to scan for rootkits and within archives, which makes the process longer but more comprehensive.
Malwarebytes is an extremely convenient malware removal software. You just install it and let it do its job. It has one complete scan scheduled daily by default and it protects from malicious websites and all sorts of attacks. Malwarebytes allows to download a free 14-day trial. But note, that after it expires, it is still very useful.
It downgrades to a free version which provides remediation (or sanitation) of threats but no real-time protection. It still works great. For users who are not too tech savvy, we’d advise not to try custom scan option, as well as automatic restart option - not to lose your work in other programs. Although, a restart after a scan is recommended to complete the malware removal process.
Though, we recommend upgrading to Premium. It is worth it, as real-time protection really makes a difference. Two great features are also available for Premium users: anti-ransomware and anti-exploit. Besides, scan scheduling has more options and is more flexible.
A great way to use Malwarebytes is to have it in combination with an antivirus. Malwarebytes labs regularly test most popular antiviruses for compatibility and update the list of software which runs well alongside, for private and business use. For example, Avast and Kaspersky will do just fine.
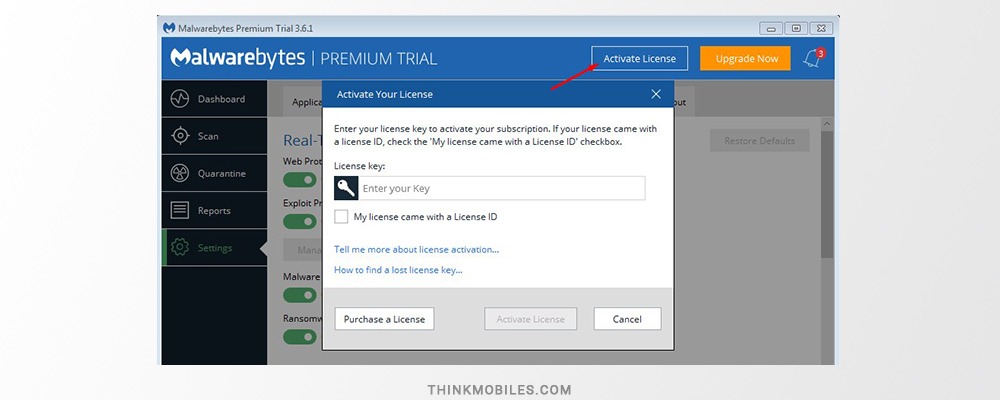
Activation. To activate Malwarebytes you should be logged into Windows as administrator. Select a Malwarebytes version you want to buy, order, and a license key will be delivered in order confirmation email. Download and install the program if you have not done it yet. Run it and find “Activate License” in the upper right part of the window. Enter a license key (if you got it with ID, check the appropriate box and enter the ID number). Click Activate License.
Quarantine. During the scans, files or programs categorized as threats are removed from the location where they were found and placed in quarantine. They are modified to eliminate the possibility of causing damage to computer. You can view the list of these files in the Quarantine tab, where you also can choose to delete or restore items. Also, be aware that sometimes Malwarebytes categorizes files as malicious incorrectly, so be attentive to what you delete from quarantine.
Application Logs. In previous Malwarebytes version 2, there is access to logs in a History tab, to read, copy and export them. In recent version, find them in the Reports section. A list of real-time protection detections is also displayed there, click twice on the log or select it and click “View report”. You also can export that information.
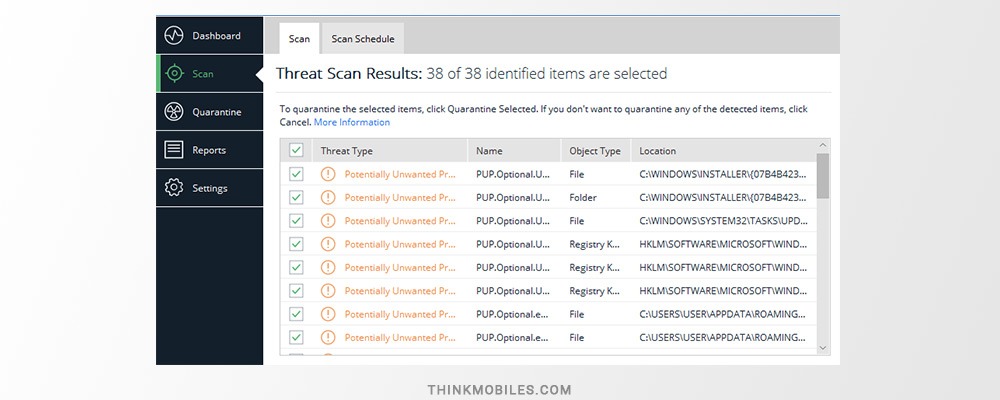
We ran the recommended - the most thorough - Threat Scan which lasted 27 minutes. While it was running, we continued working on PC: editing pictures in Photoshop and searching for some information on the Internet. We didn’t notice any slow downs in performance.
In result, Malwarebytes found 38 threats among 30,3827 scanned objects, most of them - PUPs. We studies the list of items - there were no misplaced files and we even found remains of a malware which we have been trying to eliminate for months before and were unable to. Everything worked very fine. Also, earlier, Google was constantly warning about suspicious traffic from the computer - now we do not encounter this problem anymore.
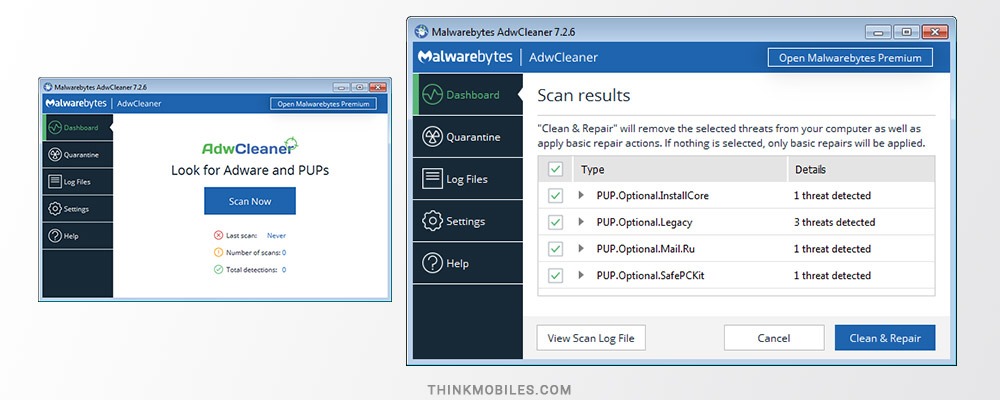
Adware can download or display advertisements on the infected device, collect marketing behavior data, and even affect user’s search requests. AdwCleaner by Malwarebytes is a separate app to download and it targets adware, spyware and potentially unwanted programs. Also, it removes unnecessary browser toolbars which you can’t remember installing because it was bundled with other software and imposed without permission. Impact on memory and processor power is insignificant. AdwCleaner scans everything in a couple of minutes and delivers results which a user can check in logs and observe in improved computer performance.
Malwarebytes is a must today. It is certainly dominant over most of other anti-malware software that ain’t got as many features and often cause issues, e.g. slowing a computer, long-time scanning, incompatibility with antiviruses, etc. The paid version is not cheap but it is worth if one wishes to effectively protect a device and not worry about attacks, vulnerabilities exploits, ransoms. Malwarebytes is generally easy to use. Advanced features may take longer to understand, and for unsophisticated users, it might be difficult to deal with files improperly marked as malicious. But there’s a support service to help anytime.
Year
Year