Conhost.exe (Console Application Host) is one of the Windows components responsible for CSRSS (Client Server Runtime SubSystem) and command prompt launch. By default, the system should run as many conhost.exe processes as command prompts. Often it is missing or gets corrupted, so let’s talk about ways to fix conhost.exe errors.
File information:
| Name | conhost.exe |
| Size | 865 Kb (Windows 10) |
| Type | Win32 EXE |
| Operating system | Windows 32-bit |
| Directory | C:\Windows\System32 |
| Software Developer | Microsoft Corporation |
| Description | Console Window Host |
| File Version | 10.0.15063.0 |
| Modification date | 2019/3/19 |
Possible causes include malware/virus infection, accidental removal, and incorrect process startup. There are several types of viruses that can disguise as a Conhost process, but most often these are Trojans hijacking system resources for cryptocurrency mining.
The difference between the original process and the virus is quite easy to spot. A virus would load the CPU by 75% or more. The original system file is usually located in the System32 folder, if not – it is a reason to check it.
Virus description:
| Name | conhost.exe virus |
| Virus type | Cryptocurrency miner, Trojan |
| Antivirus detections | AVG (Win32:DangerousSig [Trj]), Microsoft (TrojanProxy:Win32/ Bunitu!rfn), Kaspersky (Trojan.Win32.RunDll.ddu) |
| Symptoms | System errors, high CPU usage, performance drop |
| Distribution | Cracked software, online ads, email spam, etc. |
| Damage | Hardware damage, increased CPU temperature, etc. |
How to know what conhost process is original?
Very often, users encounter a problem when multiple identical processes occur in the system. If the processes are radically different in such parameters as – location, CPU, RAM, and GPU usage, it’s evident that some of them are hostile. Here are some easy ways to determine the original system process:
- Method 1
Use Task Manager (Ctrl+Shift+Esc) as a primary source of information for any specific file. First of all, pay attention to file location. Typically, all Windows system files are located in C:\Windows\System32. Then look at the process description and digital signature (Windows 10 only). Note that most system processes use the minimum amount of system resources.
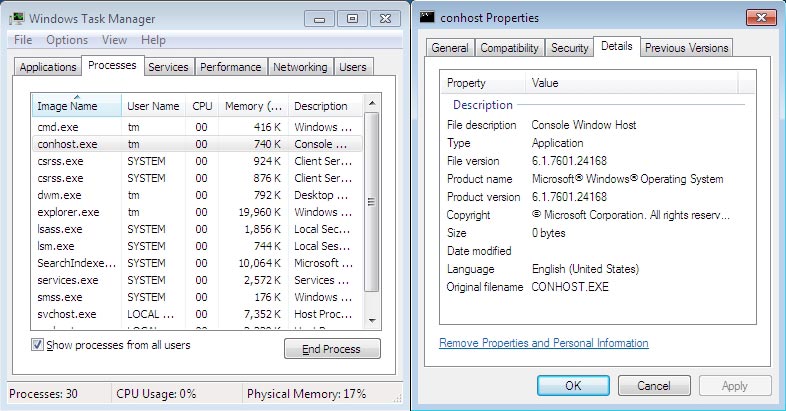
- Method 2
Use online services to check for suspicious files such as VirusTotal. Upload a file, scan it (through trusted virus databases) and view the information. Note that each file has its checksum. In our case, the scans of conhost.exe through 70 different databases did not detected any suspicious activities.
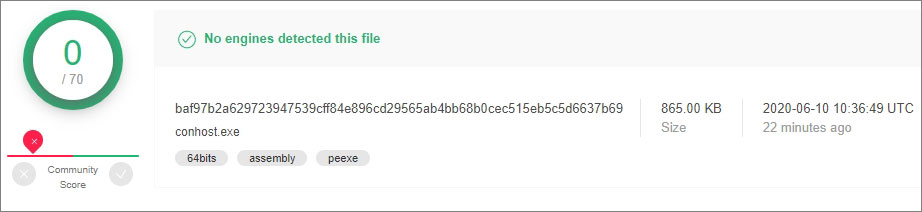
- Method 3
Check suspicious processes by a trusted anti-malware program. We recommend getting a program with a large database and real-time monitoring. Commonly, once malicious files are detected, you can delete, quarantine, or try to remedy it.
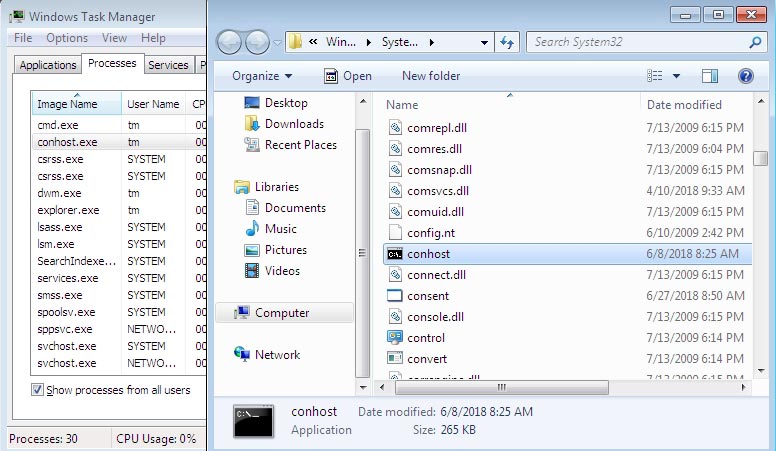
How conhost.exe was infected or deleted? Mainly, file infection could occur for several reasons: no antivirus installed, downloading files from shady websites, software installation not monitored by an anti-malware program. The process of infection is unambiguous – once a virus enters the system, it begins downloading and replacing files.
How to fix conhost.exe errors: 4 options
To fix the errors associated with this file, you must first determine the cause. You can use the built-in utility by Windows – Resource Monitor. It allows you to keep track of all processes, it’s kind of an advanced Task Manager, with more detailed information. There are several ways to run this program:
- Go to Start and enter Resource Monitor in the search line;
- Go to Start>Windows System>Run / (Win+R), type in resmon and press Enter;
- Go to C:\Windows\System32 , find the perfmon.exe file and run it.
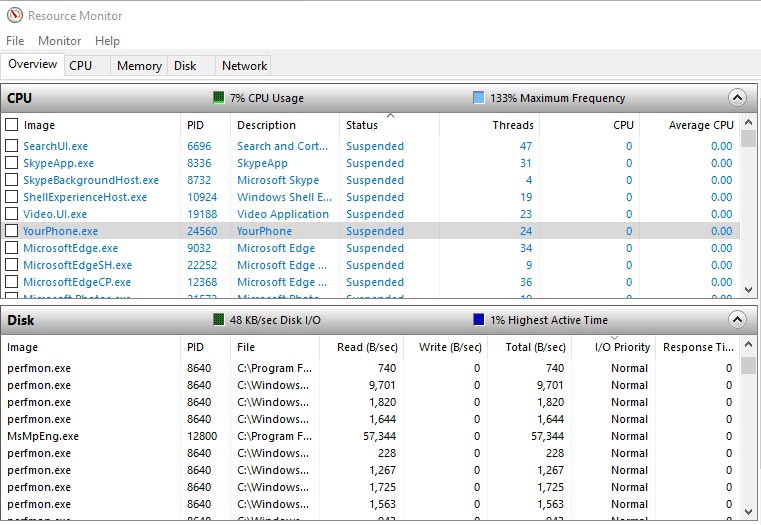
- Option 1
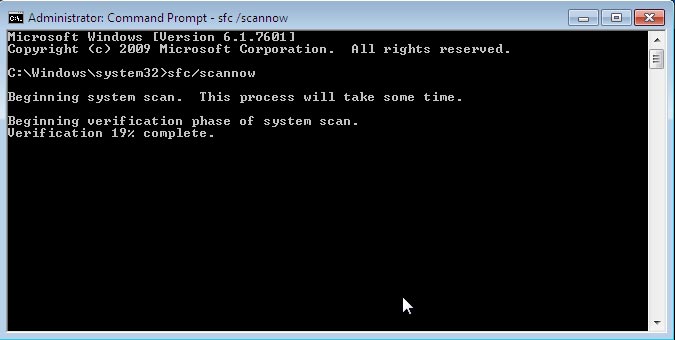
Run System File Checker to recover the infected conhost file. This Windows feature is built into Windows XP, Vista, 7, 8, 8.1, 10. To start it, press Win+R, type cmd, but also before the beginning press Ctrl+Shift (as administrator) and Enter. In the new window, enter the following command – sfc / scannow. The utility will start scanning and offer ways to solve errors. Use commands to complete the process.
- Option 2
If errors occur when the OS is launching, check what programs are also set to auto-run. We recommend disabling utilities that cause problems. To disable, open Task Manager (Ctrl+Shift+Esc), and go to the Startup tab. Reinstalling troublesome programs may help.
- Option 3
The built-in Windows option – Troubleshooter can also help to fix conhost.exe file errors. Go to Start> Settings> Update & Security> Troubleshoot and select the category you want to check. It’s recommended to run in Windows Safe Mode (Win+R>msconfig> Boot>Safe Boot field) and reboot the system.
- Option 4 (Recommended for advanced users)
If conhost.exe is missing, download it from a trusted source. Keep in mind this could be dangerous, even more so when it comes to system files. Improper system file configuration may lead to an irreversible crash of OS as a whole.
How to avoid virus infections?
Try to use licensed software only, because there are numerous malicious programs embedded in cracked versions, repacks, etc. Do not open emails from strangers. Avoid any kinds of unfamiliar websites, and use effective antivirus with active (real-time) scan mode. If you suspect file infection, perform a full scan of the system. For prevention, such inspections should be performed regularly.
How to prevent conhost errors?
#1 Perform a full scan of the system with an antivirus.
Here is a short list of top security software: IObit Malware Fighter, Avast Free Antivirus, MalwareBytes, iolo System Mechanic, Emsisoft Anti-Malware.
#2 Optimize operating system.
As a rule, it entails disabling unnecessary processes at the start, cleaning the registry, closing unused apps, etc. There are special PC optimizers for assistance. A typical program scans a PC and offers items/areas to optimize, or protect users, monitor processes. A shortlist includes: IObit Advanced SystemCare, Wise Care 365, Glary Utilities, Advanced System Optimizer.
#3 Remove unnecessary/unused programs and components.
To uninstall programs, go to Start>Settings>Apps>Apps & features. Select and remove those applications that are no longer in use, as well as suspicious ones potentially installed by other processes. After deleting, we recommend running a PC optimizer app to get rid of any traces and/or junk files.
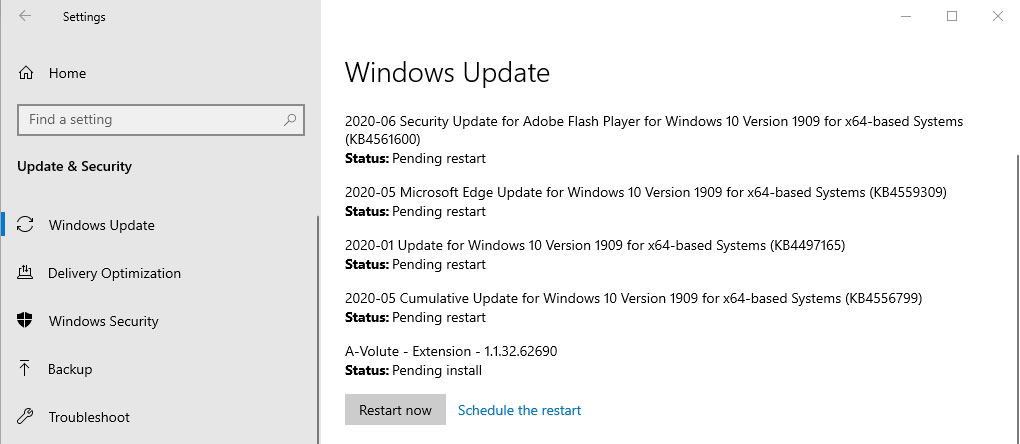
#4 Perform regular OS updates.
Windows OS usually upgrades automatically, though if disabled, you have to do it manually. Go Start> Settings> Update & Security> Windows Update. This could help fix conhost.exe issues as well.
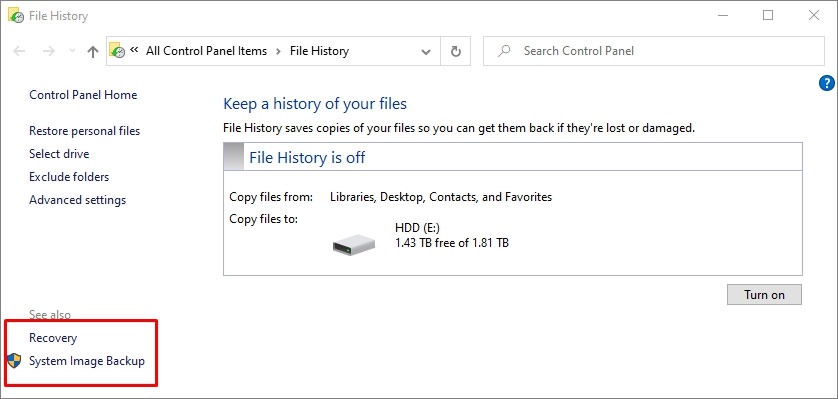
#5 Create system backups.
To backup your system, go to Start> Settings> Update & Security> Backup. You can save the working point of any disk and create an image of it. It can be used to restore the operating system and data in case of any malfunction.
Read next: How to update drivers (Guide).

